Rapid Prototyping for Cybersecurity in Mil-Tech
3-days MilTech design challenge
Client
NDA
Services
Visual Design
UI & UX Design
Industries
MilTech
Cybersecurity
Date
March 2023
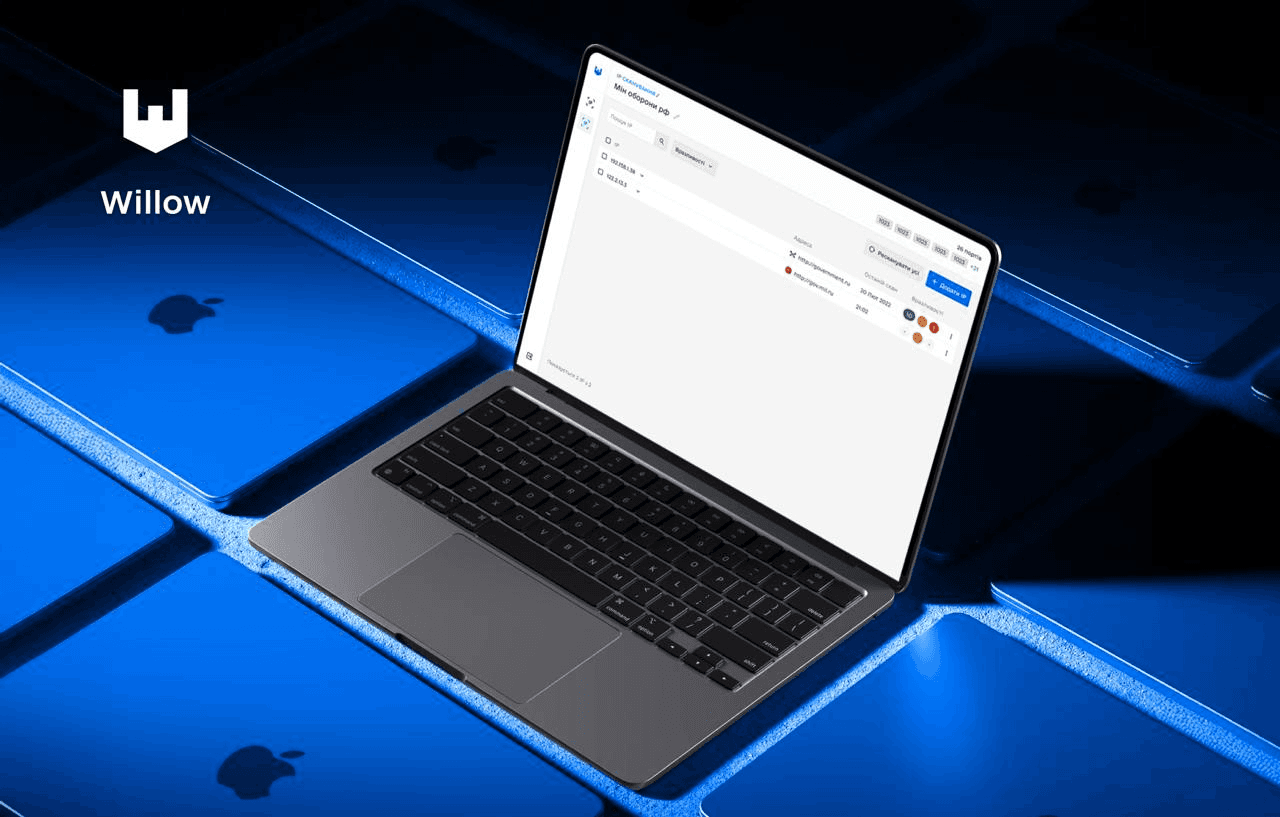
Project Overview
As a Product Designer, I explored and designed a product concept to address security and operational challenges in digital infrastructure during a fast-paced, long, non-public defense tech hackathon.
About Product
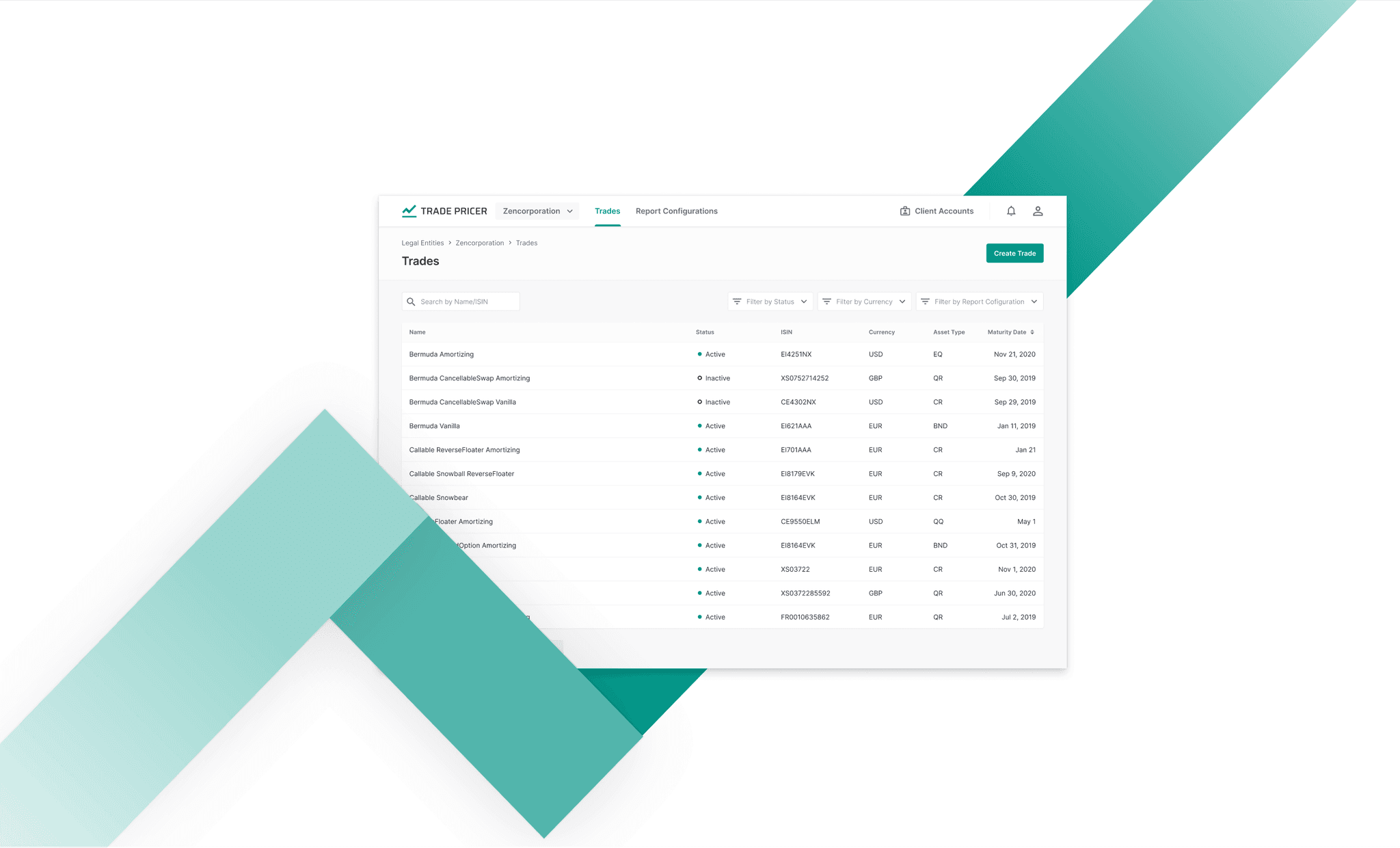
This project provides a unified platform designed to monitor and analyze vulnerabilities across web portals, both protected and those belonging to criminals that the client combats.
About Client
Client details remain confidential due to NDA agreements. The Client expressed a strong interest in innovative cybersecurity solutions and building active-defense systems to monitor and protect web resources.

Problems & Goals
Problem Statement
The Client faced the absence of a unified tool for monitoring vulnerabilities in web portals. Currently, processes are performed manually: lists of IP addresses and ports are transferred, scans are manually launched using specialized software, and people track results.
This leads to difficulties in creating reports, controlling security status changes, planning, and tracking the whole process. The lack of automation complicates the workflow, especially when rapid response to new threats is required.
Project Goal
To create an integrated system that consolidates all necessary functions into a single tool.
This will enable more efficient report creation and distribution and improve web portals' overall productivity and security.
Solution
A design concept and prototype focus on providing a glance view of the vulnerability monitoring and analysis features. It allows users to easily configure scans, view categorized vulnerabilities, and receive notifications about new threats.
The interface simplifies complex processes, making them accessible to users with varying technical knowledge (pen-testers, managers, and other users without technical experience).
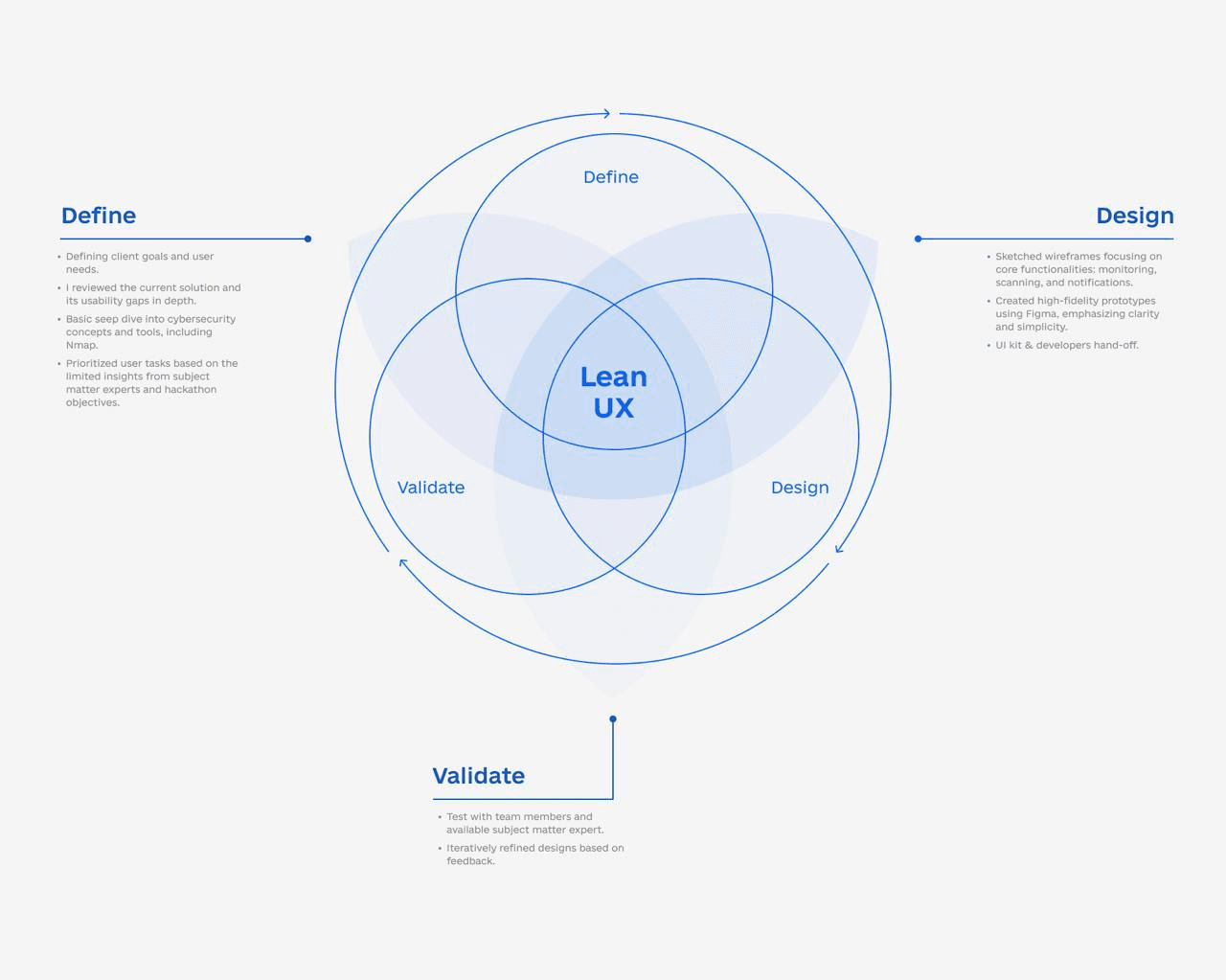
My Approach
I followed an adjusted HCD process with a Lean UX twist. It helped me empathize with users, design a solution that best suits their needs, and promptly deliver the most value to Clients in very tight timeframes.
Key Challenges & Design Decisions
Understanding Web Threats
Creating an interface for the vulnerability scanner workflow required a deep understanding of their functionalities and presenting the results in a user-friendly manner.
With the help of the subject matter expert, I've learned more about best practices and the most common tools and workflows used in the cyber security domain.
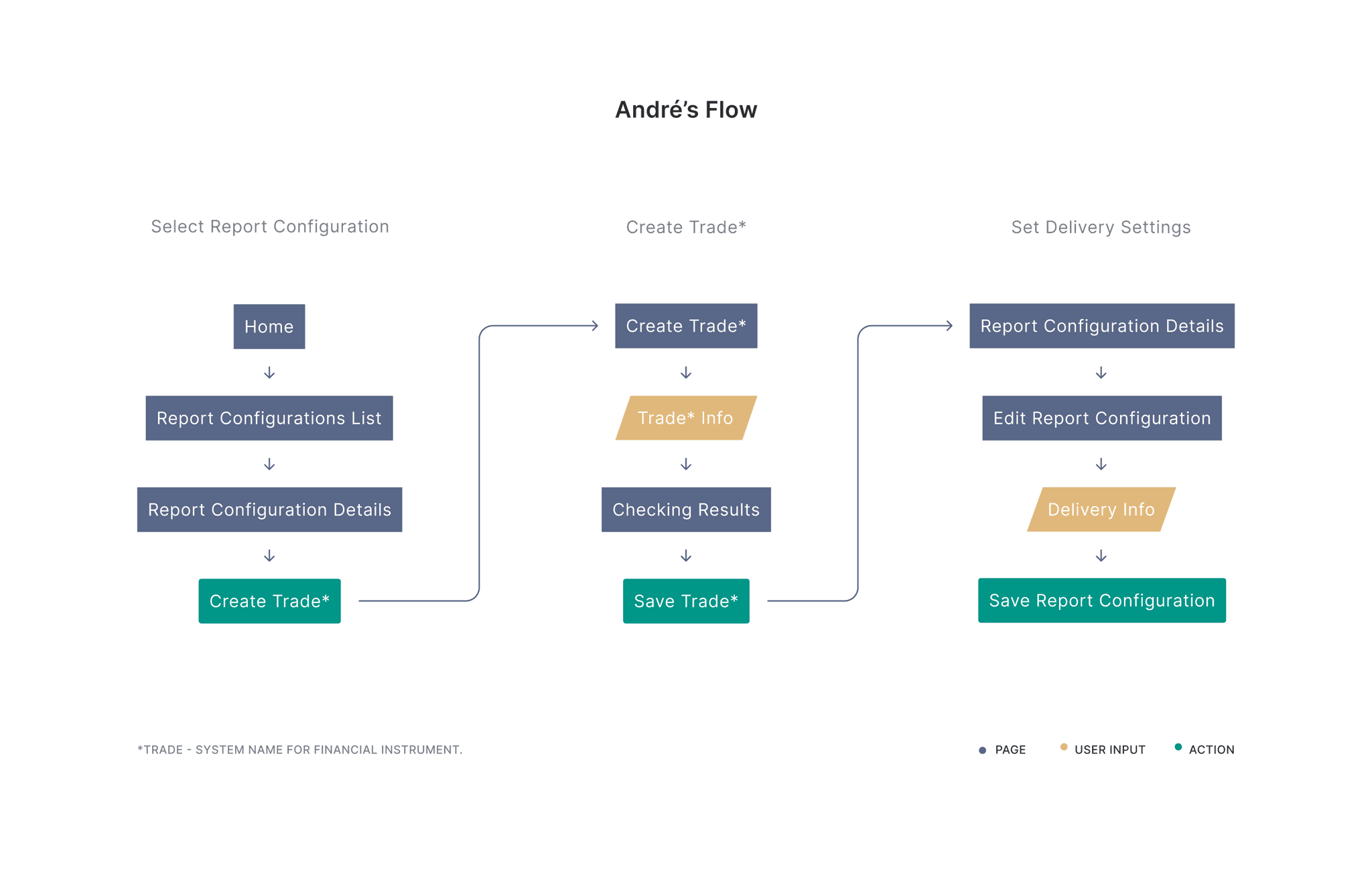
After analyzing tools involved and learning more about daily duties of pen-testes, I created a basic CJM and User Flow and aligned it with the subject matter expert.
That allowed me to get a starting point and confirm that I was on the right track before starting with actual design prototypes.
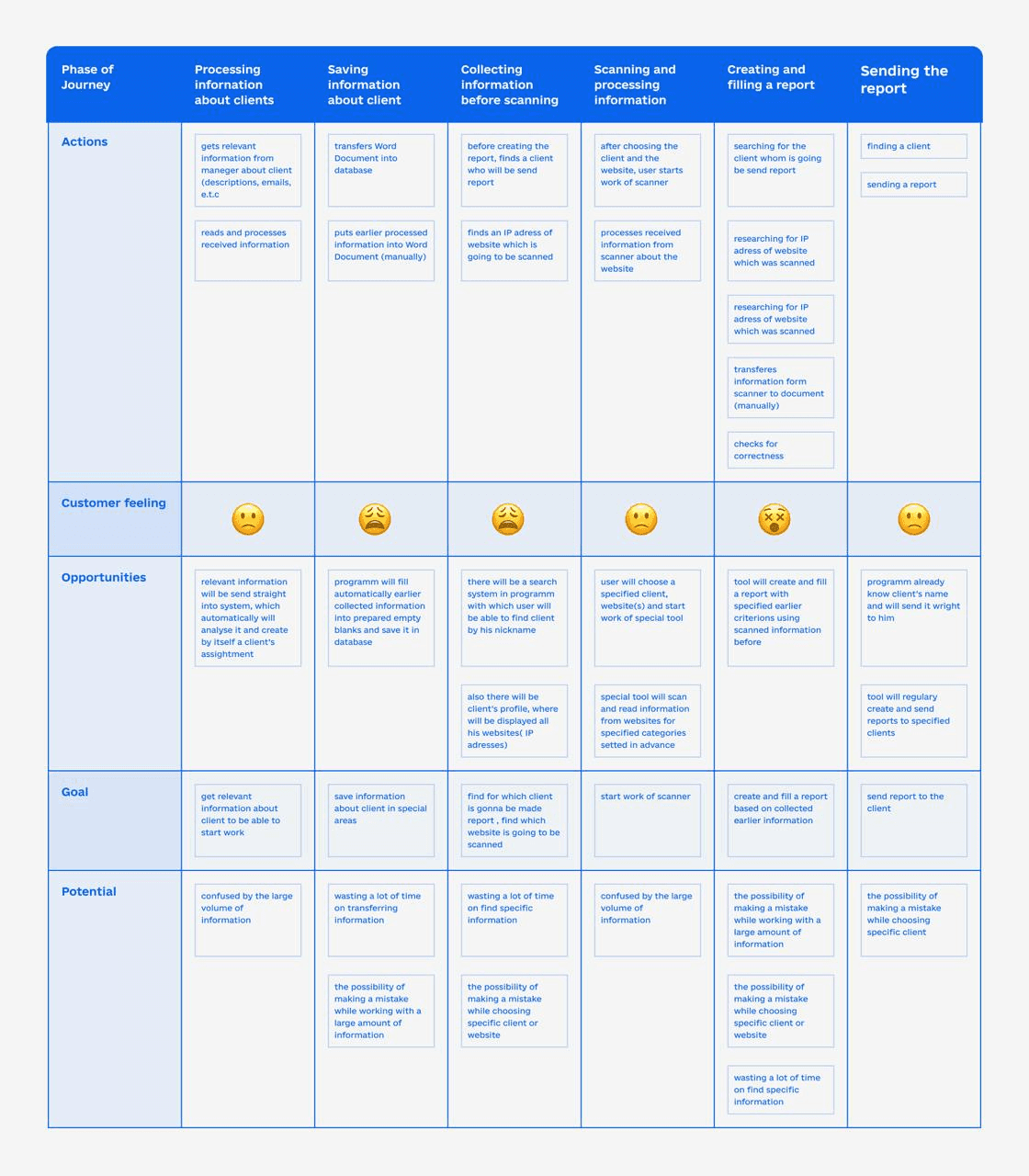
Niche-specific stakeholders
The lack of precise requirements, limited stakeholder interview time, and almost zero information about the current state of things (mostly due to security safety reasons) complicated the design process, necessitating flexible adaptation to changes.
After initial research, I decided to switch gears and use a non-usual design process to adapt to new work conditions.
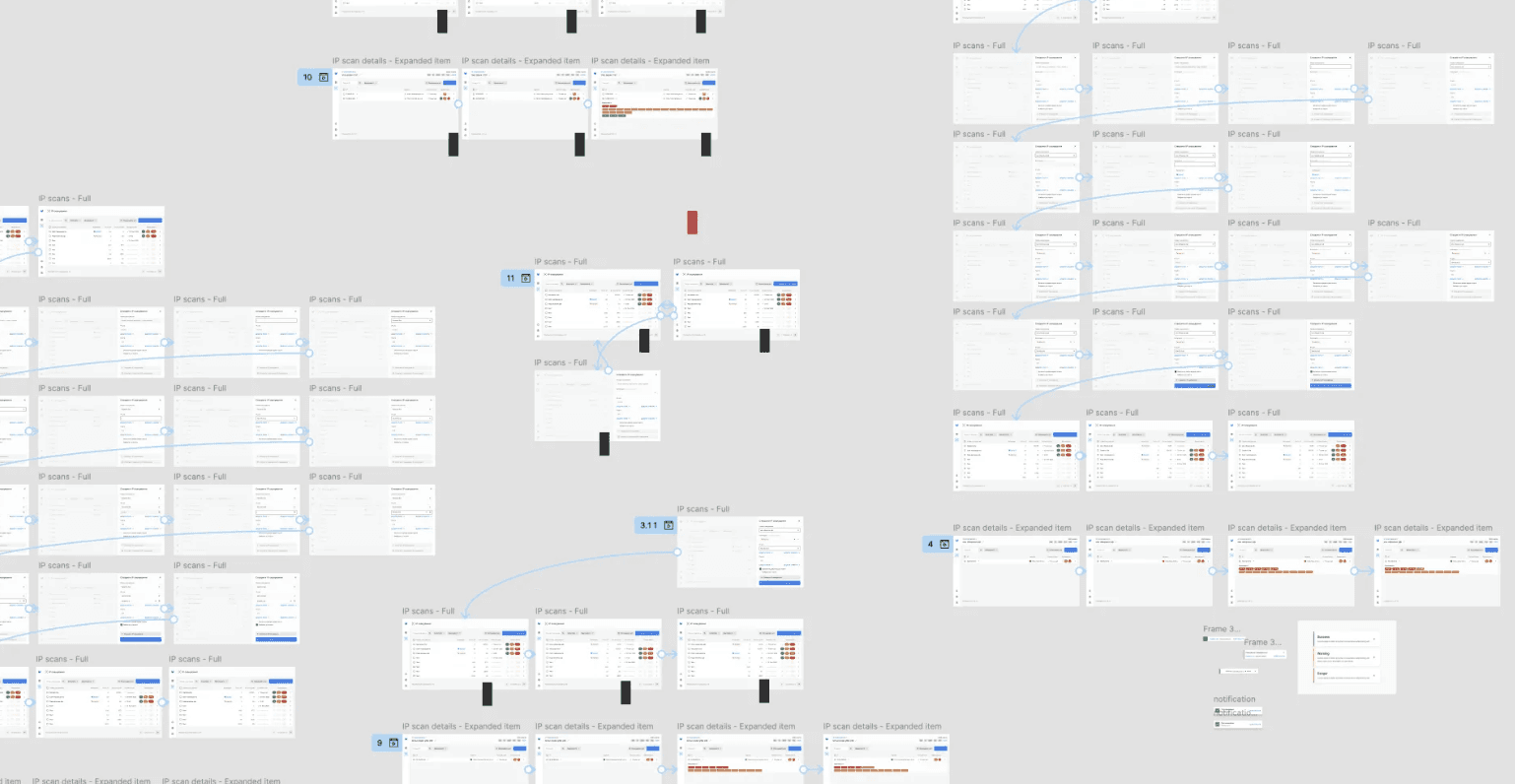
I developed low-fidelity prototypes one after another that could incorporate changes quickly, enabling effective adaptation to new requirements and receiving feedback within the hackathon's limited timeframe. Utilizing rapid prototyping allowed for swift iterations based on received feedback.
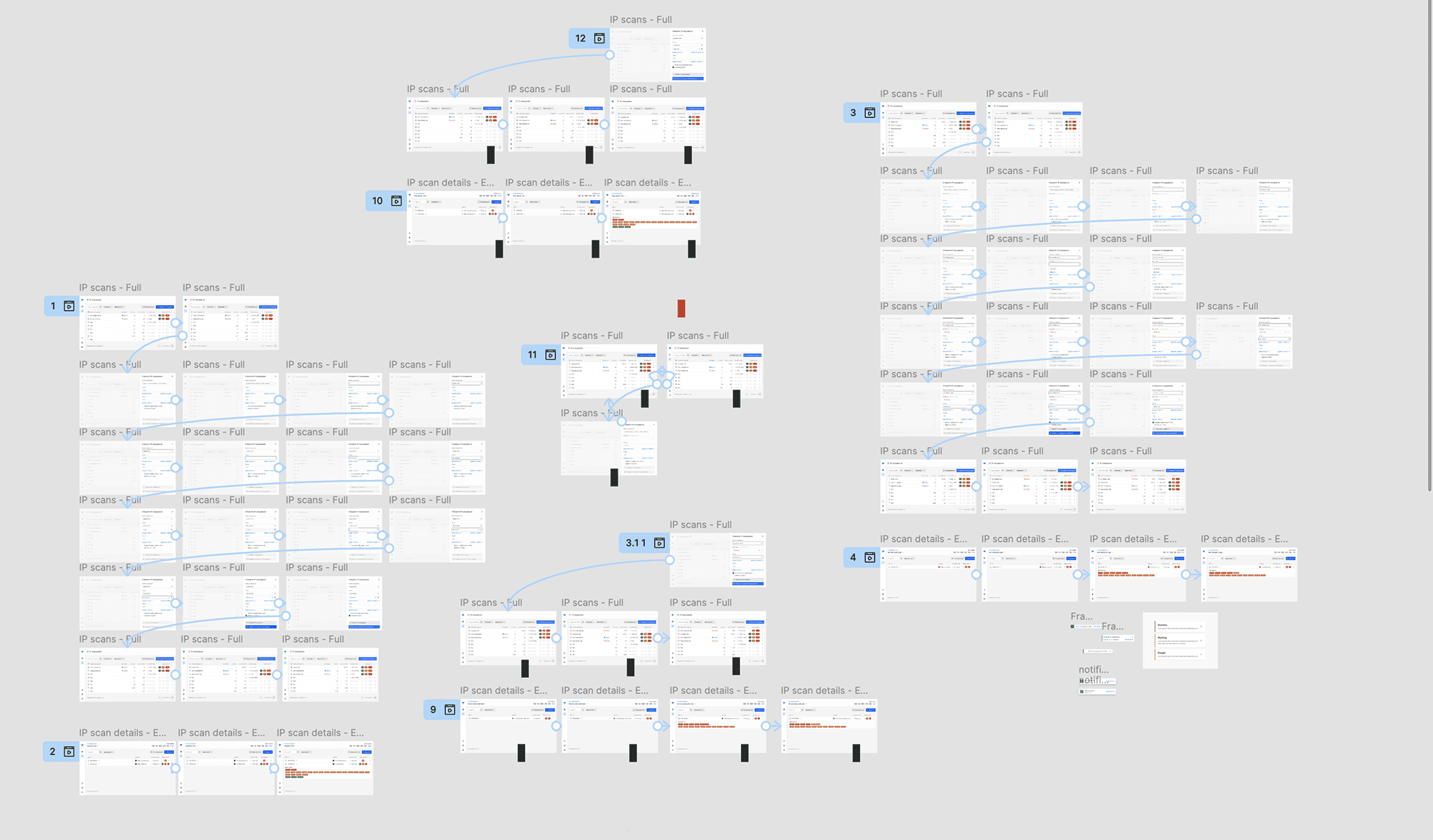
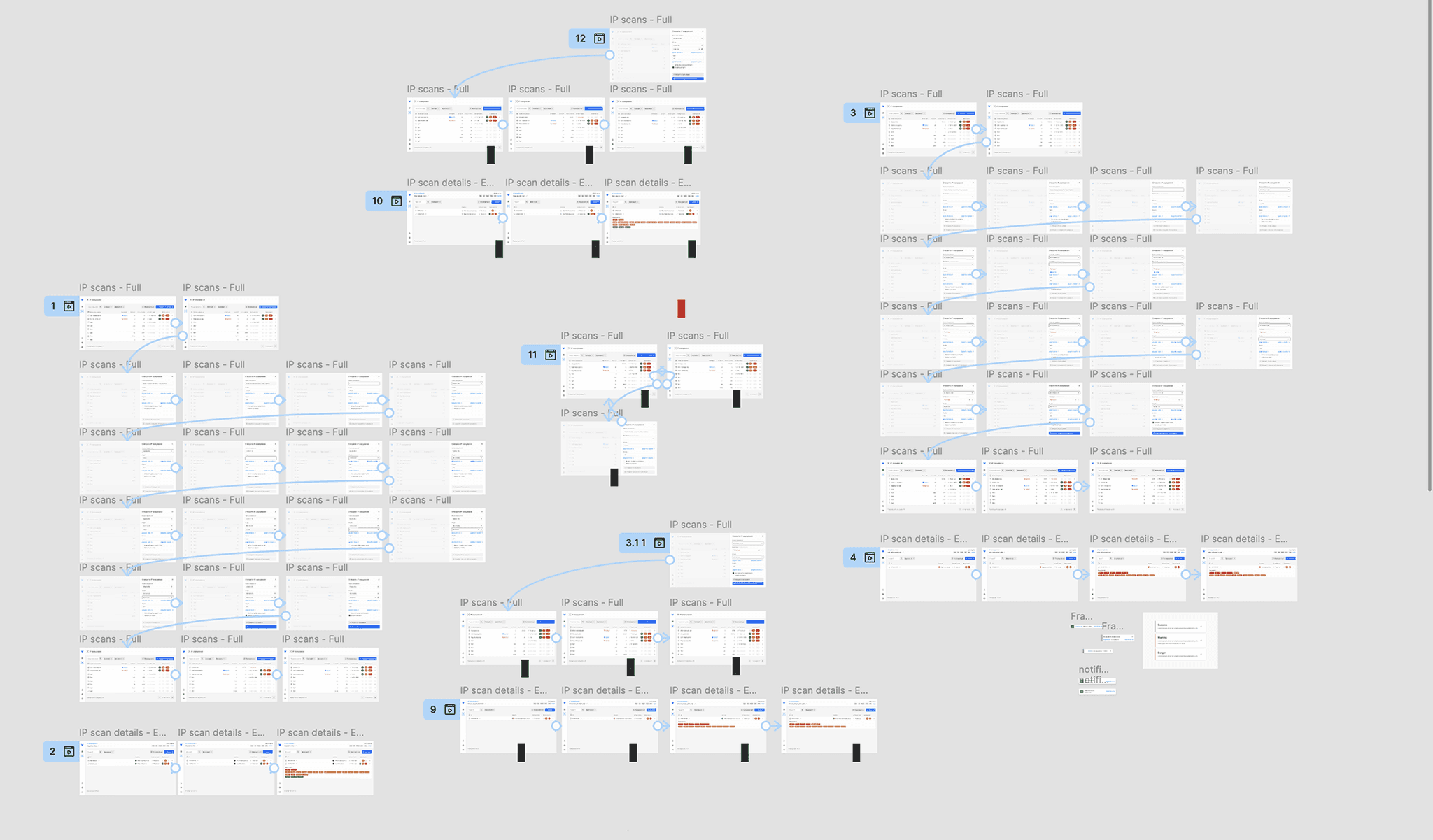
Incremental Developer Hand Off Process
Fast paced working methods during hackathons do not allow for established rich processes. Time constraints necessitated efficient resource allocation and swift feature implementation.
So, I focused on identifying and implementing only the most critical features that meet the Client's goals and users' needs.
We employed Lean-Agile methods, distributed tasks, and priorities based on page-level increments rather than features. That allowed us to parallel jobs more efficiently to meet the short deadline.
Rapid prototyping techniques and regular team check-ins facilitated quick iterations and design improvements.
Summary Outcome
Results
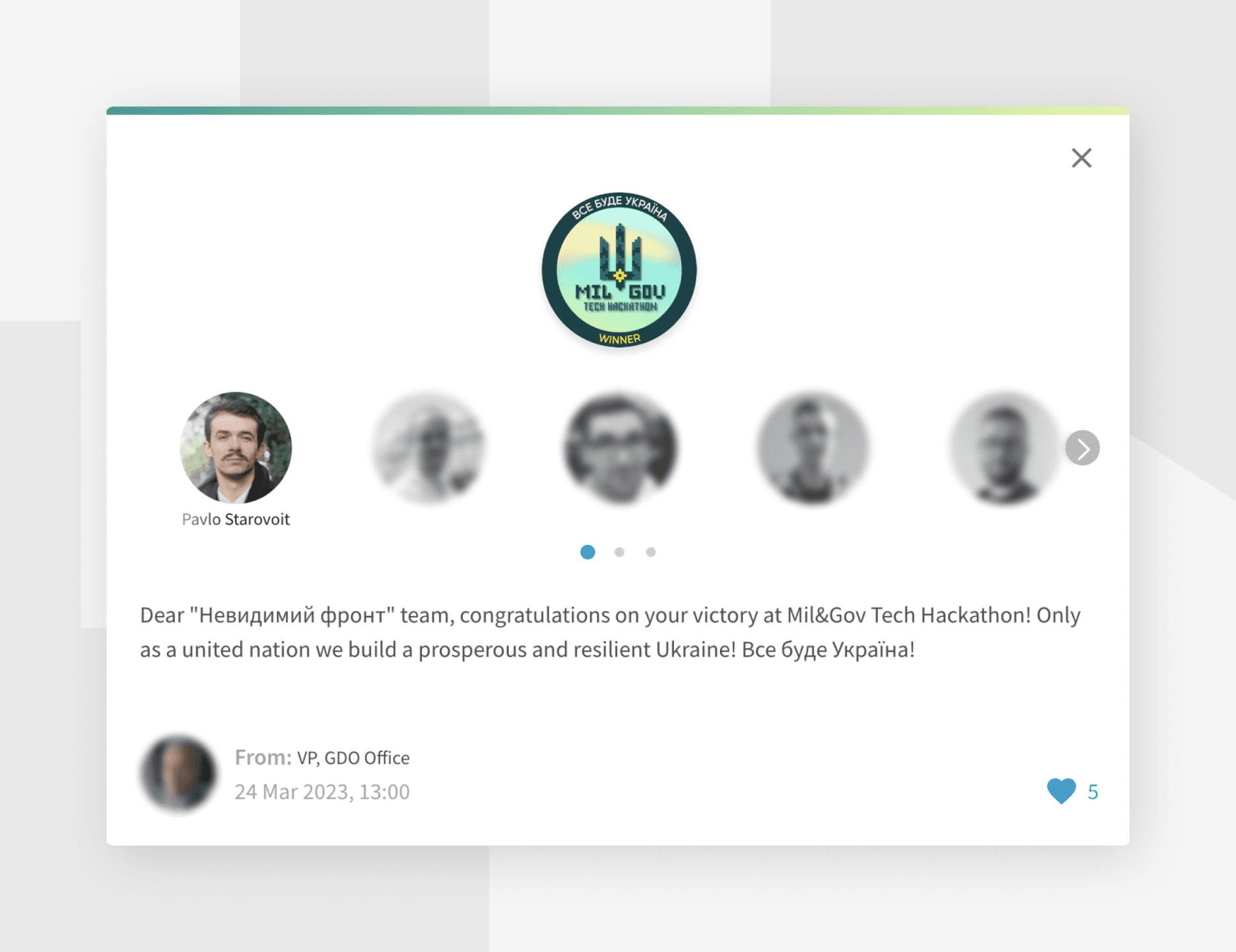
The project won the hackathon, securing first place by jury decision due to its innovative approach and practical design, and praised technical solutions that demonstrated alignment with tasks, innovation, and real potential for rapid deployment.

"As a result of the hackathon, we have interesting solutions with innovative approaches. We have already outlined communication and want to continue working with the teams and the company.", - said the Client representative.
This initial concept definition design achieved the Client's offer and now being in development into a full-fledged product.
Learnings
This initiative broadened my understanding of cybersecurity domain and defence tech in general, honed my research skills, and improved my ability to adapt to new technologies and work conditions.
I learned to work effectively under conditions of uncertainty and limited resources, significantly improving my ability to tackle complex design challenges.
Completing the project and securing first place in the hackathon highlighted the solution's potential and validated the strategic choices made throughout the design process.
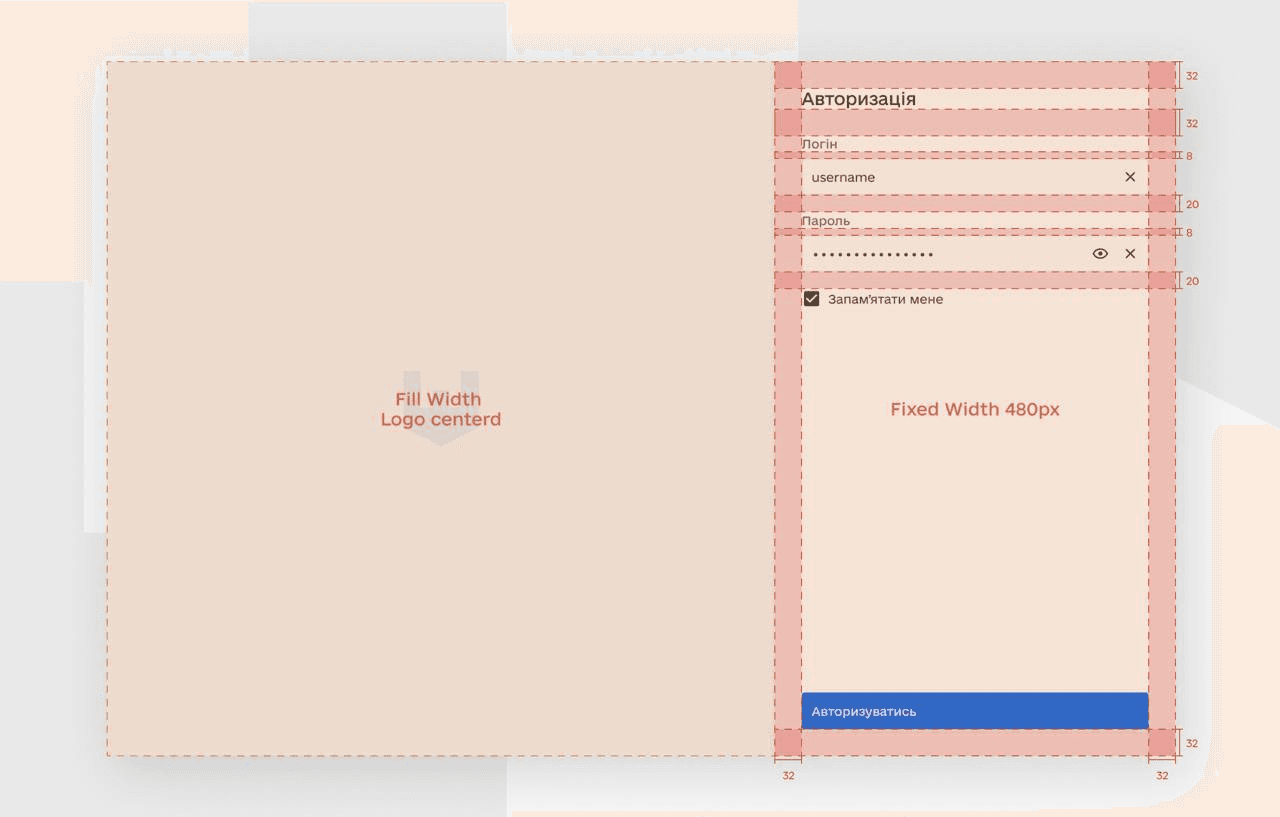
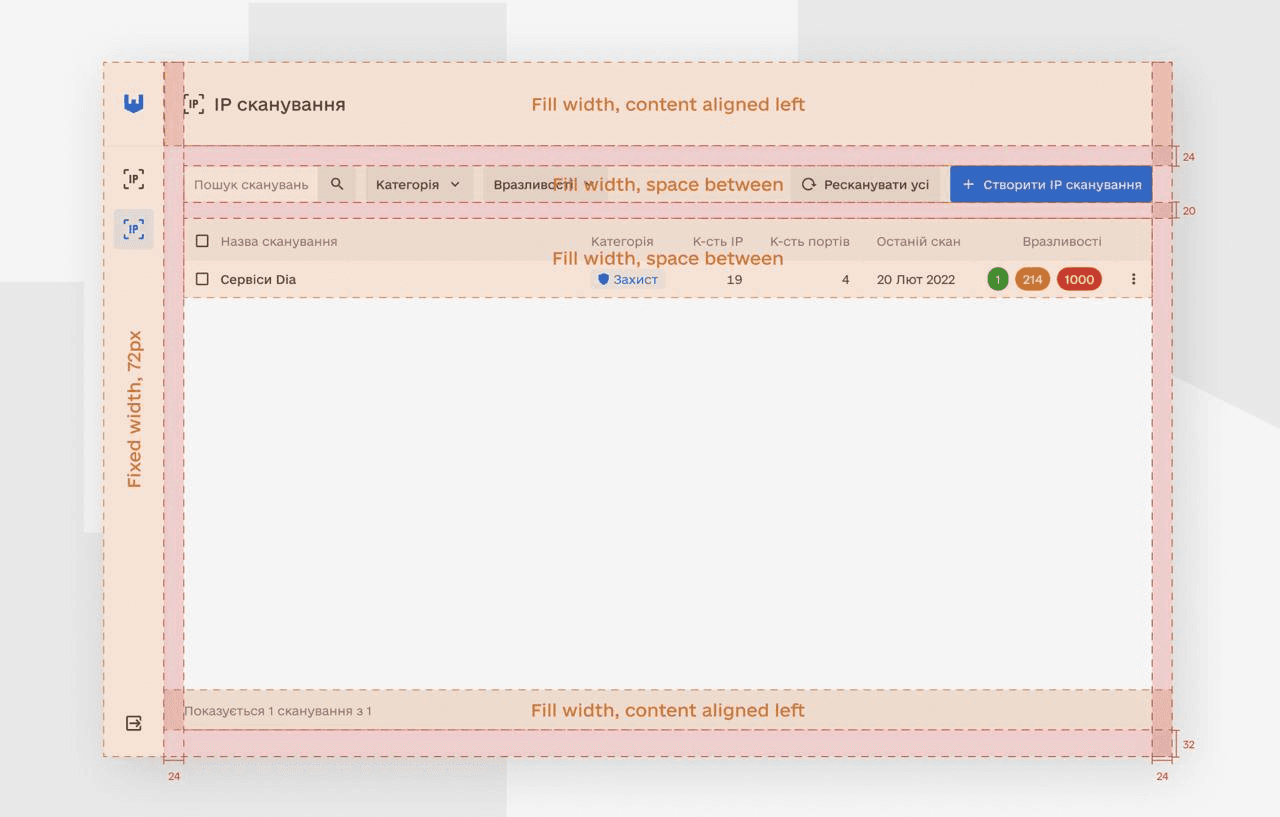
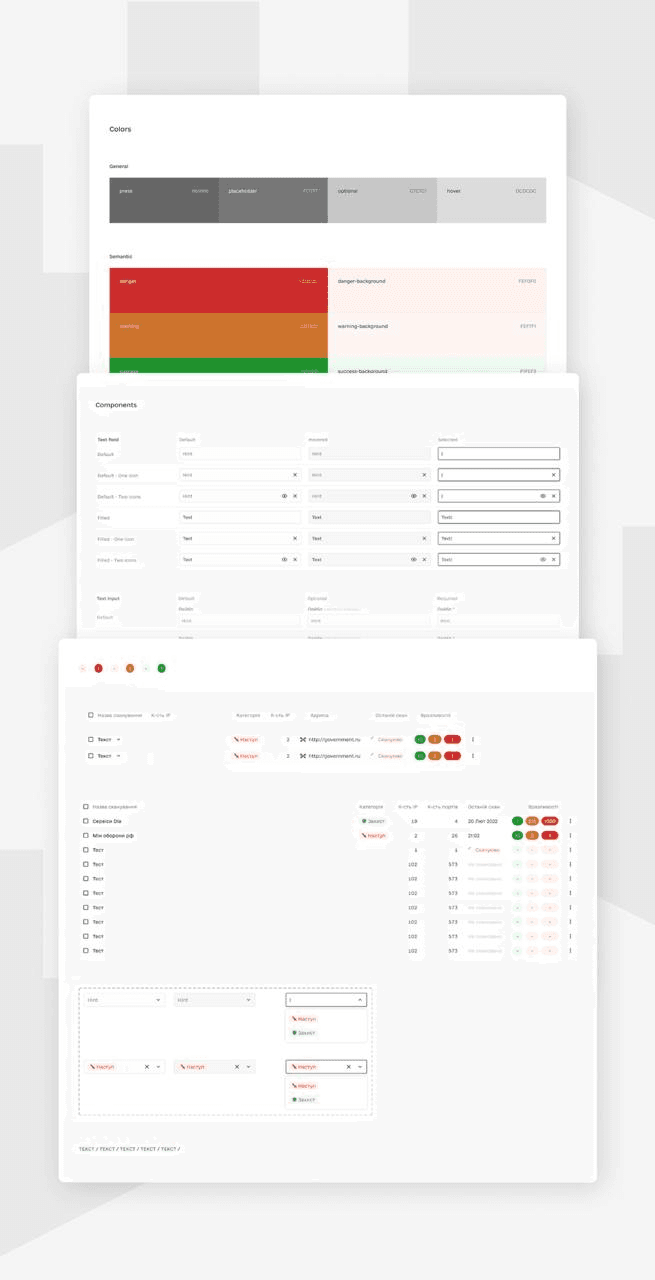
Mockups
Through extensive user research, we discovered that many e-bike users felt overwhelmed by the technology and controls on their bikes. To address this, we created a simple and intuitive interface that allows riders to easily adjust their level of assist and monitor their battery life. We also incorporated GPS navigation, allowing riders to plan their route and track their progress.
Through extensive user research, we discovered that many e-bike users felt overwhelmed by the technology and controls on their bikes. To address this, we created a simple and intuitive interface that allows riders to easily adjust their level of assist and monitor their battery life. We also incorporated GPS navigation, allowing riders to plan their route and track their progress.



Problems & Goals
Problem Statement
The Client faced the absence of a unified tool for monitoring vulnerabilities in web portals. Currently, processes are performed manually: lists of IP addresses and ports are transferred, scans are manually launched using specialized software, and people track results.
This leads to difficulties in creating reports, controlling security status changes, planning, and tracking the whole process. The lack of automation complicates the workflow, especially when rapid response to new threats is required.
Project Goal
To create an integrated system that consolidates all necessary functions into a single tool.
This will enable more efficient report creation and distribution and improve web portals' overall productivity and security.
Project Overview
About Product
This project provides a unified platform designed to monitor and analyze vulnerabilities across web portals, both protected and those belonging to criminals that the client combats.
About Client
Client details remain confidential due to NDA agreements. The Client expressed a strong interest in innovative cybersecurity solutions and building active-defense systems to monitor and protect web resources.
As a Product Designer, I explored and designed a product concept to address security and operational challenges in digital infrastructure during a fast-paced, long, non-public defense tech hackathon.
Solution
A design concept and prototype focus on providing a glance view of the vulnerability monitoring and analysis features. It allows users to easily configure scans, view categorized vulnerabilities, and receive notifications about new threats.
The interface simplifies complex processes, making them accessible to users with varying technical knowledge (pen-testers, managers, and other users without technical experience).
My Approach
I followed an adjusted HCD process with a Lean UX twist. It helped me empathize with users, design a solution that best suits their needs, and promptly deliver the most value to Clients in very tight timeframes.




Niche-specific stakeholders
The lack of precise requirements, limited stakeholder interview time, and almost zero information about the current state of things (mostly due to security safety reasons) complicated the design process, necessitating flexible adaptation to changes.
After initial research, I decided to switch gears and use a non-usual design process to adapt to new work conditions.
I developed low-fidelity prototypes one after another that could incorporate changes quickly, enabling effective adaptation to new requirements and receiving feedback within the hackathon's limited timeframe. Utilizing rapid prototyping allowed for swift iterations based on received feedback.


Incremental Developer Hand Off Process
Fast paced working methods during hackathons do not allow for established rich processes. Time constraints necessitated efficient resource allocation and swift feature implementation.
So, I focused on identifying and implementing only the most critical features that meet the Client's goals and users' needs.
We employed Lean-Agile methods, distributed tasks, and priorities based on page-level increments rather than features. That allowed us to parallel jobs more efficiently to meet the short deadline.
Rapid prototyping techniques and regular team check-ins facilitated quick iterations and design improvements.

Summary Outcome
Summary Outcome
Results
The project won the hackathon, securing first place by jury decision due to its innovative approach and practical design, and praised technical solutions that demonstrated alignment with tasks, innovation, and real potential for rapid deployment.
Key Challenges & Design Decisions
Understanding Web Threats
Creating an interface for the vulnerability scanner workflow required a deep understanding of their functionalities and presenting the results in a user-friendly manner.
With the help of the subject matter expert, I've learned more about best practices and the most common tools and workflows used in the cyber security domain.
After analyzing tools involved and learning more about daily duties of pen-testes, I created a basic CJM and User Flow and aligned it with the subject matter expert.
That allowed me to get a starting point and confirm that I was on the right track before starting with actual design prototypes.
Mockups



Learnings
This initiative broadened my understanding of cybersecurity domain and defence tech in general, honed my research skills, and improved my ability to adapt to new technologies and work conditions.
I learned to work effectively under conditions of uncertainty and limited resources, significantly improving my ability to tackle complex design challenges.
Completing the project and securing first place in the hackathon highlighted the solution's potential and validated the strategic choices made throughout the design process.
"As a result of the hackathon, we have interesting solutions with innovative approaches. We have already outlined communication and want to continue working with the teams and the company.", - said the Client representative.
This initial concept definition design achieved the Client's offer and now being in development into a full-fledged product.
Rapid Prototyping for Cybersecurity in Mil-Tech
3-days MilTech design challenge
Client
NDA
Services
Visual Design
UI & UX Design
Industries
MilTech
Cybersecurity
Date
March 2023






Through extensive user research, we discovered that many e-bike users felt overwhelmed by the technology and controls on their bikes. To address this, we created a simple and intuitive interface that allows riders to easily adjust their level of assist and monitor their battery life. We also incorporated GPS navigation, allowing riders to plan their route and track their progress.
Through extensive user research, we discovered that many e-bike users felt overwhelmed by the technology and controls on their bikes. To address this, we created a simple and intuitive interface that allows riders to easily adjust their level of assist and monitor their battery life. We also incorporated GPS navigation, allowing riders to plan their route and track their progress.
Mockups
Mockups
Rapid Prototyping for Cybersecurity in Mil-Tech
3-days MilTech design challenge
Client
NDA
Services
Visual Design
UI & UX Design
Industries
MilTech
Cybersecurity
Date
March 2023


Project Overview
About Product
This project provides a unified platform designed to monitor and analyze vulnerabilities across web portals, both protected and those belonging to criminals that the client combats.
About Client
Client details remain confidential due to NDA agreements. The Client expressed a strong interest in innovative cybersecurity solutions and building active-defense systems to monitor and protect web resources.
As a Product Designer, I explored and designed a product concept to address security and operational challenges in digital infrastructure during a fast-paced, long, non-public defense tech hackathon.


Problems & Goals
Problem Statement
The Client faced the absence of a unified tool for monitoring vulnerabilities in web portals. Currently, processes are performed manually: lists of IP addresses and ports are transferred, scans are manually launched using specialized software, and people track results.
This leads to difficulties in creating reports, controlling security status changes, planning, and tracking the whole process. The lack of automation complicates the workflow, especially when rapid response to new threats is required.
Project Goal
To create an integrated system that consolidates all necessary functions into a single tool.
This will enable more efficient report creation and distribution and improve web portals' overall productivity and security.
Solution
A design concept and prototype focus on providing a glance view of the vulnerability monitoring and analysis features. It allows users to easily configure scans, view categorized vulnerabilities, and receive notifications about new threats.
The interface simplifies complex processes, making them accessible to users with varying technical knowledge (pen-testers, managers, and other users without technical experience).
My Approach
I followed an adjusted HCD process with a Lean UX twist. It helped me empathize with users, design a solution that best suits their needs, and promptly deliver the most value to Clients in very tight timeframes.


Key Challenges & Design Decisions
Understanding Web Threats
Creating an interface for the vulnerability scanner workflow required a deep understanding of their functionalities and presenting the results in a user-friendly manner.
With the help of the subject matter expert, I've learned more about best practices and the most common tools and workflows used in the cyber security domain.
After analyzing tools involved and learning more about daily duties of pen-testes, I created a basic CJM and User Flow and aligned it with the subject matter expert.
That allowed me to get a starting point and confirm that I was on the right track before starting with actual design prototypes.


Niche-specific stakeholders
The lack of precise requirements, limited stakeholder interview time, and almost zero information about the current state of things (mostly due to security safety reasons) complicated the design process, necessitating flexible adaptation to changes.
After initial research, I decided to switch gears and use a non-usual design process to adapt to new work conditions.
I developed low-fidelity prototypes one after another that could incorporate changes quickly, enabling effective adaptation to new requirements and receiving feedback within the hackathon's limited timeframe. Utilizing rapid prototyping allowed for swift iterations based on received feedback.


Incremental Developer Hand Off Process
Fast paced working methods during hackathons do not allow for established rich processes. Time constraints necessitated efficient resource allocation and swift feature implementation.
So, I focused on identifying and implementing only the most critical features that meet the Client's goals and users' needs.
We employed Lean-Agile methods, distributed tasks, and priorities based on page-level increments rather than features. That allowed us to parallel jobs more efficiently to meet the short deadline.
Rapid prototyping techniques and regular team check-ins facilitated quick iterations and design improvements.






Summary Outcome
Results
The project won the hackathon, securing first place by jury decision due to its innovative approach and practical design, and praised technical solutions that demonstrated alignment with tasks, innovation, and real potential for rapid deployment.


"As a result of the hackathon, we have interesting solutions with innovative approaches. We have already outlined communication and want to continue working with the teams and the company.", - said the Client representative.
This initial concept definition design achieved the Client's offer and now being in development into a full-fledged product.








